A road-map to basic Internet Privacy & Security
I thought I could maybe offer a “quick-digest” of sorts to make you, the “everyday internet user”, just a little more privacy & security aware.
I thought I could maybe offer a “quick-digest” of sorts to make you, the “everyday internet user”, just a little more “privacy & security aware”.
Now, these are some pretty basic topics, most of which I have already covered on my blog/newsletter, in detail. If you think this is too basic, hold on, stay with me. I assure you, an awareness of these topics would make you several notches better than the average internet user (in terms of privacy and security).
🎥FourZeroThree - YouTube
Heads up! Did you know I also run a YouTube channel by the same name “FourZeroThree”? I try to create short and entertaining videos out of the articles I post. Don’t forget to check it out!
Passwords
Passwords are the most common and fundamental means of authentication in most services on the web. Since, this is the case, its important you use secure (complex and lengthy) passwords for every service/website you register to.
Let’s summarize what you could do to implement a good password strategy.
Bad actors/hackers use offline password cracking tools that could mathematically guess millions to billions of password combinations per second. Hence create complex and lengthy passwords that are hard to mathematically guess.
Alternatively, use “passphrases” if complex passwords are hard to remember.
Never reuse passwords, however complex and lengthy they might be. You never know when a website/service (you registered to), would be hacked and your credentials breached! Regularly use haveibeenpwned to check if your credentials have been breached or not.
Don’t save all your passwords in a word or text document. They are going to be in plain text. Encrypt them.
💡Use Password Managers
Use password managers to generate and auto-fill secure passwords for you. Let it do the heavy-lifting. This would be the best option for a secure password practice.
2 Factor Authentication (2FA)
Assuming your password could be hacked, why not have another factor that helps an application/website verify it is indeed you? Using another factor of verification besides a password, allows you to have an extended layer of security. Google’s security research found that activating 2FA helped prevent automated bots, phishing attacks and targeted attacks.
Most websites usually use your mobile device (to verify you) as a second factor of authentication. The website either sends a one-time password (OTP) to your mobile device via SMS or it would make use of mobile authenticator applications like Google Authenticator or Authy. Websites would verify you via soft tokens/time-based one-time passwords (TOTP) generated by these apps.
Your email is extremely sensitive and is very important to protect, especially if you primarily use a single email address to sign up everywhere. Most websites/applications use services like email, to help reset passwords. If your email is hacked, it is game over! Irrespective of whether you use 2FA for other services, for god’s sake protect your email additionally with 2FA.
Even if you have 2FA activated, 1) make sure you use a password manager to generate secure passwords and 2) do not reuse passwords! Don’t get complacent.
💡Use 2FA wherever possible
Secure your account with 2FA wherever possible, especially your email, banking, shopping, and social media accounts.
Email Strategies
Email hygiene is often neglected by average users. Most do not consider an email address to be sensitive information. Email has sort of, become indispensable these days with most websites making it mandatory for registration. Using just one or maybe two email addresses across several websites is not secure practice.
Websites (not all websites) may sell your email information to 3rd party companies or data mining companies. You could subsequently be bombarded with spam and unsolicited emails.
If a website you use is breached, hackers could get hold of the only email address you use for all other services too. There is risk of hackers trying to guess your password across commonly used websites with your email address or worse, your email account itself being targeted.
Your email being breached also means you would be a target to phishing attacks.
Here are some actionable tips you could make use to maintain email hygiene.
Share your personal email address only with friends and family, never with anyone else you may deem to be outside of your first circle. Most importantly do not register to services/websites with your personal email address.
Have a separate email account for banking and other financial services. Again, never use this email address for any other purpose.
Have a separate email address for registering for social media services/websites.
For e-commerce, newsletters, and other junk or random websites, use fake email addresses.
💡Use Burner Email services
If you think you have too many email IDs to handle, make use of burner email services. I use a service called Anonaddy (Edit: I use SimpleLogin these days). Michael Bazzell of inteltechniques.com recommends a few more in this podcast episode. You could create burner email addresses/aliases on the fly and use them without risking giving away your real email address (you could learn how-to here).
So, maybe you could have 3 separate email addresses tied to your real name, for personal, banking, and social media purposes. For the rest, use burner email addresses.
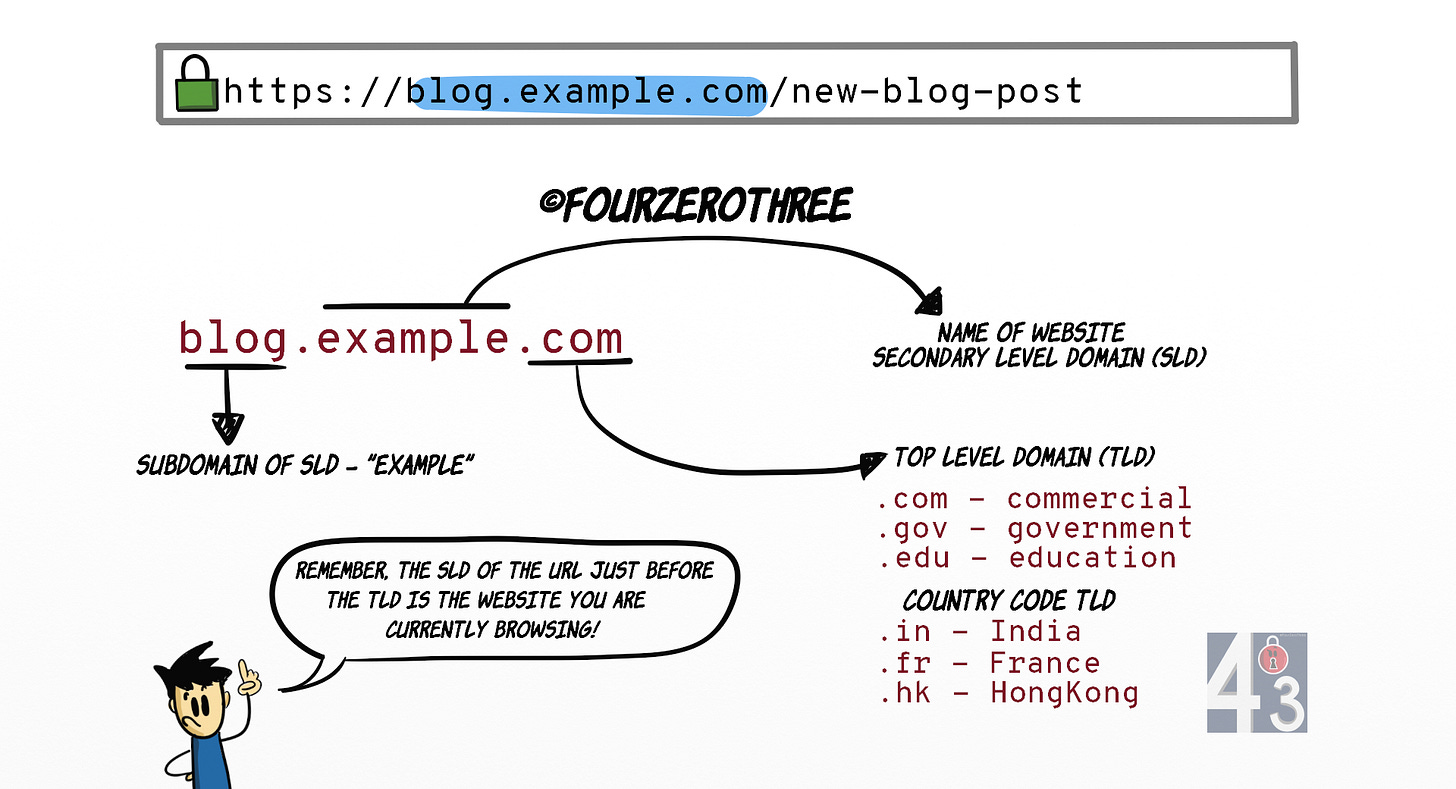
Know the basics of how a “URL” is structured
💡Knowledge/awareness of how a URL is structured could help you be secure when faced with certain malicious situations, like phishing. There are bad actors out there trying to scam you into clicking fake/malicious URLs/links.
Always check if a website has implemented Transport Layer Security (the “S” in HTTPS). You would know this when you see a “padlock” besides “https” on the address bar.
Know the difference between the main/primary domain name and a subdomain. For instance, in a URL like example[dot]com, example[dot]com is the main/primary website. Whereas, in a URL like blog[dot]example[dot]com, “blog” is the subdomain of the main domain “example[dot]com”.
Armed with this awareness, you could recognize a scammer trying to pose as someone legitimate. For example, support[dot]example[dot]com is legit “Example Inc”. Whereas, example[dot]support[dot]com, may be a scam website (here support[dot]com is the primary domain) trying to trick you into believing they are “Example Inc”.
You may at times encounter long URLs/links like this -> auth[dot]example[dot]com/login?redirect=example[dot]com/account. These links when manipulated could be tricky for a regular user to identify as fake or legit.
You could read this article on URLs for a deeper dive/to know more.
Third party cookies and tracking
Cookies are not evil. They are meant to make your web browsing experience seamless and personalized.
However,
Companies quickly realized that they could set their own cookies on pages belonging to other sites—with their permission and by paying for the privilege—and the third-party cookie was born.
- Data and Goliath by Bruce Schneier
If you are new to the concept of cookies or have no idea of how cookies work, I recommend you read All you need to know about cookies - Part I (How cookies work). This would give you context of how cookies work, in order to understand how corporations use 3rd party cookies to track your online behavior.
Without getting into the nitty-gritty of how 3rd party tracking (via 3rd party cookie) works lets go through some actionable tips you could incorporate to avoid being tracked online.
The first thing you could do is to change the privacy options in your browser. Modify the settings such that your browser blocks third party cookies and other trackers.
Firefox browser as an example…
You could set your browser such that it deletes all your cookies (including first-party) on closing it. However, this is a trade-off for convenience. Since this also deletes your first-party cookies, you would have to log in manually to every website every time you open a new session on your browser.
Use privacy browser extensions/addons like UBlock Origin and Privacy Badger (both available for Firefox and Chrome) to help block online tracking.
You could use privacy-focused browsers like “Brave”. Brave browser blocks ads and tracking by default. It is also actively experimenting on counteracting fingerprinting.
Use privacy-focused search engines like “DuckDuckGo”.
Browser Compartmentalizing
In addition to the above steps you could take to minimize online tracking, you could go one more step further and compartmentalize your browsing habits. That is, to use different browsers for different browsing contexts.
Exclusively have an “accounts” browser (for the sake of an example, Chrome browser). Use this browser for services you may have log in to, like social media, email, and banking etc. Do not use this browser for anything else. Bookmark these websites and use the bookmarked link to directly head to them.
Use another browser with privacy extensions/addons (Brave, maybe) for research/reading and in general to browse websites of interest to you.
Use another browser with privacy extensions/addons (Firefox, maybe) for junk or random browsing.
Use a browser exclusively for shopping/e-commerce.
You could either browse in “Incognito Mode” or browse normally by configuring your browser to delete all cookies and browsing history on closing.
💡The idea here is to spread your browsing habits over different browsers, so that it becomes difficult for 3rd party corporations to make an accurate browsing profile of you.
Social Engineering
Any act that influences a person to take an action that may or may not be in their best interest.
- https://www.social-engineer.org/
While social engineering does not always cater to something negative, lets discuss ways you could mitigate a social engineering attempt to scam/cheat you. Bad actors could try to scam you by
Phishing - eliciting sensitive information or influencing action via email
Vishing - eliciting sensitive information or influencing action via voice/phone calls
SmiShing - eliciting sensitive information or influencing action via SMS
Action here would cater to making a victim
type his/her credentials in a fake website spoofing to be another legitimate company,
download malware or
visit a malicious website
Heads up! www.social-engineer.org is a great website dedicated to everything “social engineering”! You could head there to delve deeper into social engineering.
Be it phishing, vishing or smishing, bad actors try to take advantage of intrinsic human attributes like greed, panic, fear, kindness etc in order to scam victims.
Phishing
Hackers, most often, try to make victims panic with their phishing emails, so that victims are blinded to sound judgement. In the process, victims make hasty decisions, be it clicking on a link without inspecting it, entering their credentials on a fake login page or downloading an attachment having malware. Mostly, scammers try to impersonate big corporations (like Amazon, PayPal, etc) to influence action.
More on phishing:
Here are some actionable tips you could follow to prevent yourself from falling a prey to phishing attacks.
Whenever you receive an email from someone you are not familiar with or an email “seeming” to be from a popular corporation, take a minute to pause and analyze the email chunk by chunk.
First thing you do is to check the “from” email address. More often than not, it is easy to recognize a garbage “from” email address. This could be a dead giveaway.
Don’t hastily click any link in an email. Hover on the link (or long press the link in mobile) to find out the actual URL structure (the URL is displayed at the bottom left of your screen).
Check the grammar of the body of the email. If the email is supposedly from a popular/big corporation and the grammar is bad, then be rest assured that the email could be fake.
Do not download any attachment/s in an email that you receive from someone you do not recognize.
Password manager could be a life saver! A password manager saves and has a record of the websites you have registered to in their database. It would auto-fill passwords only on websites it recognizes. Even if you end up being scammed into clicking a link, to be redirected to a spoofed “log in” page, your password manager would not recognize the website and would not auto-fill your password (the fake website obviously would have a different domain name and is spoofing a legitimate website).
If the scammers end up pilfering your credentials, having 2FA enabled would help prevent your account from being taken over!
Vishing
Similar to phishing, vishing is the art of eliciting sensitive information or influencing an action via voice calls.
Bad actors may pose as sales representatives and ask for sensitive information like your email address.
Callers may claim to be from your bank, establish authority or induce panic by stating there was suspicious activity in your bank account. They would then want to verify your bank account and try to pilfer sensitive information like your email address, birth date, user ID, account number etc.
Callers may try to scam you into paying for a good charitable cause.
Scammers may tap into human greed, and claim you have won a prize or an offer and so forth.
Mitigation
Don’t trust anyone. Hang up and call your bank or whichever company the caller claimed to be from, to confirm.
Don’t trust caller IDs, they can be spoofed.
Banks don’t call you and ask for sensitive information. Its only when you want sensitive actions to be performed on your bank account, like changing your email ID or password and blocking your debit/credit card, does your bank ask for your details. After all, you want them to perform sensitive actions on your account and they have to verify who you claim to be.
Its okay to say NO or to be rude to someone you don’t recognize. Most times, it is not possible to verify who the caller claims to be. Remember not to give out any information that is tied to you personally.
Smishing
SmiShing is almost like phishing emails, only difference being the medium where you receive the message, via SMS on your mobile device. The messages induce you into calling a fraudulent phone number or clicking malicious links that may download malware or direct you to a malicious website.
Mitigation
Don’t trust messages, if you do not recognize or cannot verify the source.
Don’t click links in haste. Check to see if they are genuine.
Resources
Here are some great resources you could read to up your privacy and security game!
Hiding from the Internet: Eliminating Personal Online Information by Michael Bazzell
Data and Goliath – The Hidden Battles to Collect Your Data and Control Your World by Bruce Schneier
Schneier on Security - Bruce Schneier’s blog
Troy Hunt - Troy Hunt’s blog
Krebs on security - Brian Krebs’ blog