The fascinating World of Bug Bounty hunting - What it is and how you could get your feet wet
Application vendors or organizations run a bug bounty program that allows for security researchers or bug bounty hunters to scout for security vulnerabilities in their application/software.
I, unintentionally, came across the term “Bug Bounty” in early 2018 when I was trying to google what a brute-force attack was. After some reading, I understood on a superficial level, that organizations or application vendors ran something called a “bug bounty program'“ and rewarded ethical hackers if they found security vulnerabilities in their applications.
Clicking link after link on google, I came across a link that read “Hacktivity - Hackerone”. Clicking on the link opened a page like this.

I understood this page was a list of reports of security flaws that security researchers (bug bounty hunters) had submitted to application vendors. I’ll be honest, the first thing that caught my eye was the cash reward listed on the page beside each report. I couldn’t believe researchers were being paid for hacking (ethically and responsibly, of course). Clicking on a report’s link opened up a page where the vulnerability was discussed in detail.
Honestly, I couldn’t comprehend anything, I didn’t even know what Hackerone was. But I found it all very interesting and was excited enough to want to dig further.
🎥FourZeroThree - YouTube
A quick shout out! Here's a “video version” of the article. If you are the visual type, I recommend watching the video. I bet you’ll enjoy it :)
🤔What is a bug bounty program? Who are bug bounty hunters?
💡Application vendors or organizations run a bug bounty program that allows for security researchers or bug bounty hunters to scout for security vulnerabilities in their application/software. On reporting valid security flaws to these vendors, hackers or security researchers are compensated monetarily.
The idea behind a bug bounty program is to crowd-source security testing of an organization’s applications. Organizations have internal security teams. Some outsource security testing to private penetration testing companies. But by crowd-sourcing application testing, organizations can derive the best bang for their buck. Apart from having a few individuals in their security team monitoring their software, with a public bug bounty program, organizations potentially have more eyes, finding and reporting security flaws on a larger scale.
👨💻How does this work?
Before bug bounties were mainstream, security researchers found it hard to report vulnerabilities to organizations. Security testing without the organization’s consent was (and is still) considered illegal.
These problems were solved with the advent of Bug Bounty Platforms.
These platforms act more like marketplaces that allow free-agent bug bounty hunters and the companies that are interested in their services find each other. They attract companies by giving them access to a large pool of hackers, and in turn attract hackers by providing a list of companies that are willing to pay for their services.
- Tammy Xu, Bug Bounties: An Overview
There are quite a few bug bounty platforms very active today, some of which are
The two best-known and biggest bug-hunting organizations, HackerOne and Bugcrowd, cumulatively have raised $190.4 million of venture funding since 2011 for creating platforms that connect hackers and security researchers with organizations that offer vulnerability disclosure programs and bug bounties.
- Seth Rosenblatt, Bug Bounty Hunters' Pro Tips on Chasing Vulns & Money
Apart from Synack, anyone can register as a security researcher on the platforms listed above. Once registered, researchers have a large pool of organizations running public programs, that they could look into.
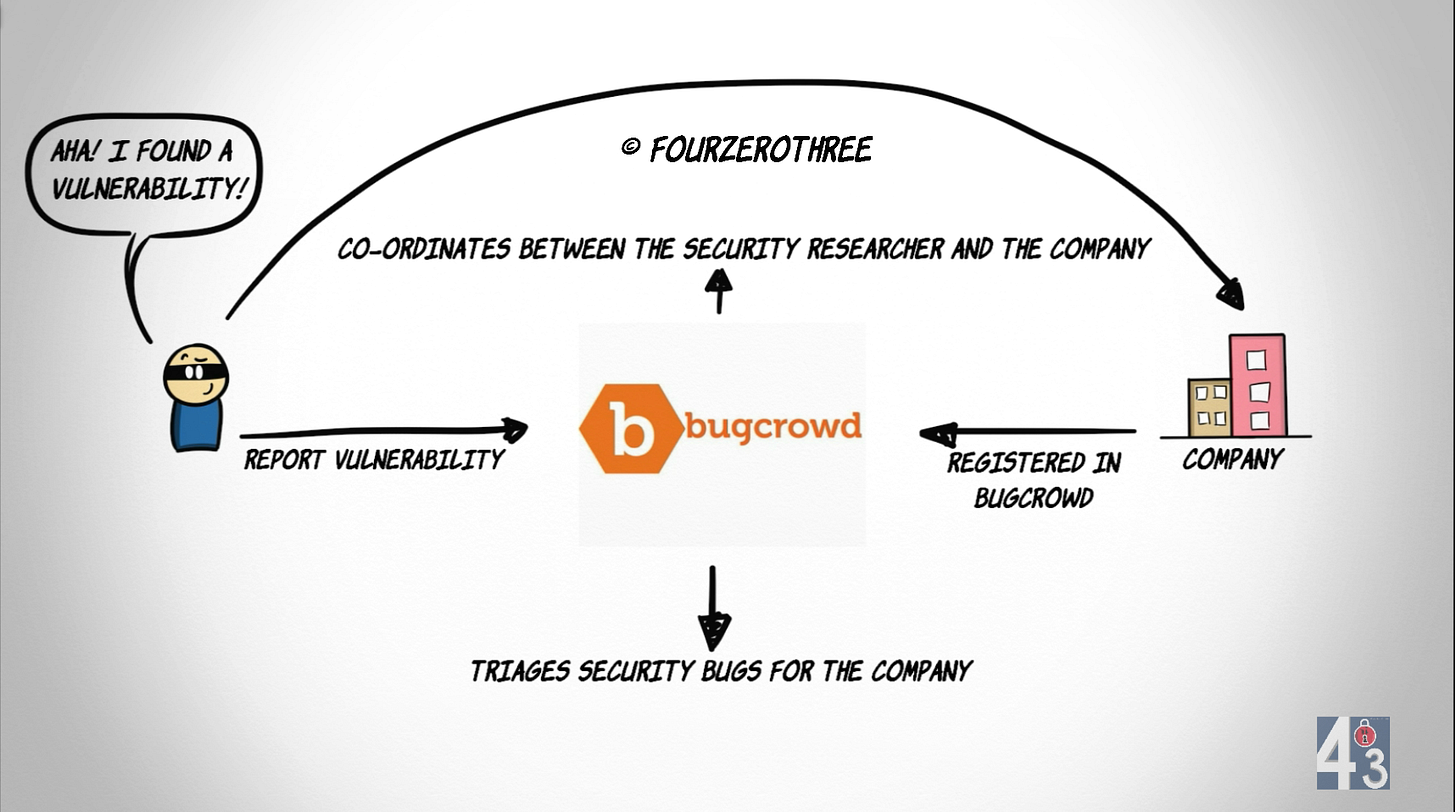
A security researcher, after finding a security flaw in an application of an organization could report to bug bounty platforms where the organization or the vendor has been listed. These platforms help organizations/vendors triage reported bugs (security vulnerabilities) and act as middle-men making co-ordination between researchers and organizations easy.
📈Rating researcher work
Bug bounty platforms, apart from coordinating reports and rewards between researchers and organizations, also award reputation points and rate researchers according to the impact of their reported vulnerabilities. Security bugs are rated as low, medium, high, and critical. The higher the impact of the bug, the more reputation points a researcher earns.
🐛Public and Private bug bounty programs
Public programs as the name suggests are public, open for any researcher to participate in. In general, public programs are very hardened as far as bugs are concerned, and finding security flaws could prove to be arduous.
Private programs are open only to selected researchers with a good track record of reporting impactful vulnerabilities. This is where the points system comes into play and skilled researchers are invited by organizations according to their points and skill set they possess (web/mobile/IoT hacking). In general an organization usually starts off with a private bug bounty program before they become hardened enough to become public.
📊Some interesting stats
Here are some interesting stats from the Hacker Report 2021 (Hackerone) and Inside the mind of a Hacker 2020 (Bugcrowd). These are studies done by Hackerone and Bugcrowd respectively, detailing the efforts and motivations of hackers and economics of the security ecosystem.
As in "Hacker Report 2021"
Hacking remains a popular pursuit for Generation Z, with 55% of the community under 25 years old. Hacking is paving the way for their future; 33% have leveraged their skills to secure a job and 23% plan to continue their career in information security within an internal security team.
Hackers earned $40 million in 2020 alone, contributing to reaching the milestone of $100 million paid out to hackers on the HackerOne platform. Nine hackers have earned over $1 million dollars on the platform since 2019, and one hacker passed the $2 million mark in 2020.
Hackers are represented across all industries, with 59% of hackers focusing on internet and online services and 47% on financial services. 41% of hackers hack on retail & ecommerce programs, and 43% hack on computer software programs.
96% of hackers work on hacking web applications, this is up from 71% last year. Elsewhere, the growth in specializations is far greater with a 694% increase in hackers saying they spend time hacking APIs, and a 663% increase in hackers focusing on Android. The greatest growth is in IoT with a 1000% increase in hackers
As in "Inside the mind of the Hacker"
Top 10 countries where respondents report living -> 1)India, 2)US, 3)Pakistan, 4)Bangladesh, 5)Indonesia, 6)UK, 7)Egypt, 8)Australia, 9)Nepal, 10)Germany
Compared to last year's report, Bugcrowd observed an 83% increase in the number of respondents who report living in India.
The majority who collected bounty payments live in India, the United States, and Canada.
Getting your feet wet in Bug Bounties
I tried my hand at bug bounties for a few months and submitted around 26 reports (with little success honestly, many were triaged to be duplicates or bugs that were already submitted by researchers). It was a wonderful experience. Eventually I started hitting a wall, which I suspect is primarily due to my lack of a deeper understanding of web technology.
If you are interested and intend to get your feet wet, here’s my two cents on what you could read, learn and do. Its up to you to fill knowledge gaps and keep the learning lamp lit.
Learn the basics
Read books
Basic Tools
Learn how to use tools like BurpSuite and Owasp Zap Proxy. This is mandatory. These would be your staple “go to” tools.
Online resources
Learn and practice with labs in “Web Security Academy” by Portswigger. I cannot emphasize this platform enough. It’s got great content and amazing real world labs you could learn from. I would recommend you start with Web Security Academy as soon as you feel comfortable with basics.
Some YouTube channels you could follow
Honestly, this list though not exhaustive is more than enough to get you started with bug bounties. Know that you would always have knowledge gaps. There is no “knowing everything”! This list here would get you as far as being a rookie. The real learning comes with actually doing bug bounties.